How to configure ufw to forward port 80/443 to internal server hosted on LAN
Iam using UFW to protect my network. How do I forward TCP HTTP port # 80 and 443 to an internal server hosted at 192.168.1.100:80 and 192.168.1.100:443 using UFW on Ubuntu Linux server?
UFW is an acronym for uncomplicated firewall. It is used for managing a Linux firewall and aims to provide an easy to use interface for the user. In this tutorial, you will learn how to forward incoming traffic to your server running ufw on port 80/443 to port 80/443 on another internal server hosted in your LAN/VLAN.
Our sample setup
Let us say you want to forward requests going to {80,443} to a server listening on 192.168.1.100:{80,443}:
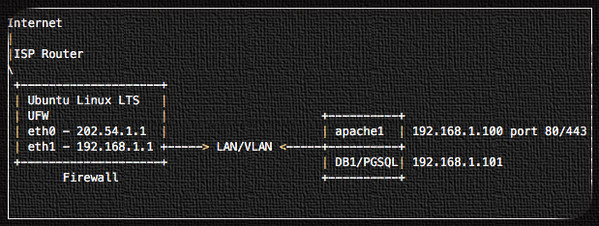
Fig.01: How to configure ufw to redirect http traffic to another IP:port
All request for 202.54.1.1 port 80 and 443 need to redirect to another internal server.
DNAT
If you have a server on your internal network that you want make available externally, you can use the -j DNAT target of the PREROUTING chain in NAT to specify a destination IP address and port where incoming packets requesting a connection to your internal service can be forwarded. The syntax is:
OR
/sbin/iptables -t nat -A PREROUTING -i eth0 -p tcp -d {PUBLIC_IP} --dport 80 -j DNAT --to {INTERNAL_IP}:80OR
/sbin/iptables -t nat -A PREROUTING -i eth0 -p tcp -d {PUBLIC_IP} --dport 443 -j DNAT --to {INTERNAL_IP}:443Postrouting and IP Masquerading
To allow LAN nodes with private IP addresses to communicate with external public networks, configure the firewall for IP masquerading, which masks requests from LAN nodes with the IP address of the firewall’s external device such as eth0. The syntax is:
OR
/sbin/iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADEOR
/sbin/iptables -t nat -A POSTROUTING -s 192.168.1.0/24 ! -d 192.168.1.0/24 -j MASQUERADEHow to configure ufw to setup a port forward
You need to edit /etc/ufw/before.rules file, enter:
Next configure ufw to redirect http traffic to another (LAN) IP:port. At the top file, append:
$ sudo vi etc/ufw/before.rulesNext configure ufw to redirect http traffic to another (LAN) IP:port. At the top file, append:
Save and close the file. Edit /etc/sysctl.conf:
Set/edit as follows:
$ sudo vi /etc/sysctl.confSet/edit as follows:
net.ipv4.ip_forward=1
Save and close the file. Reload changes:
Finally, restart the firewall to enable routing:
Make sure port 80 and 443 is allowed, otherwise ufw will block the requests that are redirected to internal 192.168.1.100:{80,443}:
Verify new settings:
Finally, make sure your domain has DNS type ‘a’ set to 202.54.1.1.
$ sudo sysctl -pFinally, restart the firewall to enable routing:
$ sudo systemctl restart ufwMake sure port 80 and 443 is allowed, otherwise ufw will block the requests that are redirected to internal 192.168.1.100:{80,443}:
$ sudo ufw allow proto tcp from any to 202.54.1.1 port 80
$ sudo ufw allow proto tcp from any to 202.54.1.1 port 443Verify new settings:
$ sudo ufw status
$ sudo iptables -t nat -L -n -vFinally, make sure your domain has DNS type ‘a’ set to 202.54.1.1.
No comments:
Post a Comment