How to open ssh port using ufw on Ubuntu/Debian Linux
How do I allow incoming SSH connections from a specific IP address or subnet on a Ubuntu or Debian Linux server using ufw?
UFW is an acronym for uncomplicated firewall. It is used for managing a Linux firewall and aims to provide an easy to use interface for the user. In this tutorial, you will learn how to use UFW a frontend to iptables for opening incoming SSH connection on Ubuntu Linux 16.04 LTS or Debian Linux server.

Fig.01: Allow Incoming SSH from Specific IP Address or Subnet
Open incoming SSH port for all
The syntax is:
OR
If you are running ssh on TCP port # 2222, enter:
sudo ufw allow sshOR
$ sudo ufw allow 22/tcpIf you are running ssh on TCP port # 2222, enter:
$ sudo ufw allow 2222/tcpHow to allow incoming SSH from specific IP address
The syntax is:
To allow incoming SSH connections from a specific IP address named 202.54.1.1, enter:
$ sudo ufw allow from {IP_ADDRESS_HERE} to any port 22To allow incoming SSH connections from a specific IP address named 202.54.1.1, enter:
$ sudo ufw allow from 202.54.1.1 to any port 22How to allow incoming SSH from specific subnets
The syntax is:
To allow incoming SSH connections from a specific IP subnet named 202.54.1.1/29, enter:
$ sudo ufw allow from {IP_SUB/net} to any port 22To allow incoming SSH connections from a specific IP subnet named 202.54.1.1/29, enter:
$ sudo ufw allow from 202.54.1.1/29 to any port 22Limit incoming SSH port for all
Open incoming SSH but deny connections from an IP address that has attempted to initiate 6 or more connections in the last 30 seconds. The syntax is:
OR
$ sudo ufw limit sshOR
$ sudo ufw limit 22/tcpHow to check the status of ufw
The syntax is:
Sample outputs:
$ sudo ufw statusSample outputs:
Status: active To Action From -- ------ ---- 22 ALLOW Anywhere 72.14.190.12 443/tcp ALLOW Anywhere 72.14.190.12 80/tcp ALLOW Anywhere
if ufw was not enabled the output would be:
sudo ufw status Status: inactive
To turn on UFW on with the default set of rules including open SSH port, enter:
$ sudo ufw enable
$ sudo ufw status verboseHow to limit SSH (TCP port 22) connections with ufw on Ubuntu Linux
How do I limit ssh connection attempts using UFW (Uncomplicated Firewall) on Ubuntu or Debian Linux server?
UFW means Uncomplicated Firewall. It defaults on Ubuntu and can be installed on other Linux distros such as Arch Linux, Debian and more. It is nothing but a front-end for managing a Netfilter firewall. It provides a command line interface and aims to be uncomplicated and easy to use.
UFW means Uncomplicated Firewall. It defaults on Ubuntu and can be installed on other Linux distros such as Arch Linux, Debian and more. It is nothing but a front-end for managing a Netfilter firewall. It provides a command line interface and aims to be uncomplicated and easy to use.

Rate limiting with ufw
You can add limit rule. Currently only IPv4 is supported. With this syntax you can deny connections from an IP address that has attempted to initiate 6 or more connections in the last 30 seconds. This option is very useful for services such as sshd.
Syntax
The syntax is pretty simple:
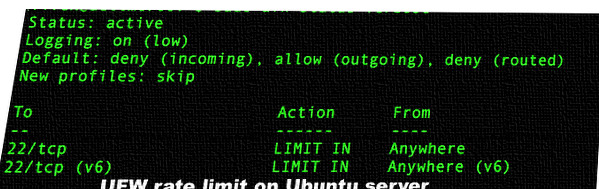
The above rules are useful for protecting against brute-force login attacks. When a limit rule is used, ufw will normally allow the connection but will deny connections if an IP address attempts to initiate six or more connections within thirty seconds. Once setup you can verify it with the following command:
Sample outputs:
$ sudo ufw limit ssh/tcp comment 'Rate limit for openssh serer'
$ sudo ufw statusSample outputs:
Status: active To Action From -- ------ ---- 22/tcp LIMIT Anywhere # Rate limit for openssh serer 22/tcp (v6) LIMIT Anywhere (v6) # Rate limit for openssh serer
The actual rules are as follows in iptables:
Please note that the new ssh rule will then replace the previous ssh rule.
No comments:
Post a Comment