The Linux and open source community provides countless user and server applications. They also provide solutions to help support these and other applications, even to support non-technical departments. You'll find here many help desk or customer service, etc. Best suited for Linux Administrator, Linux Newbies, etc... Hope my efforts helps u solving your problems!!!!!!!!
Monday, September 28, 2015
Wednesday, September 23, 2015
[Cluster Computing]: How to Configure Linux Cluster with 2 Nodes on RedHat and CentOS
How to Configure Linux Cluster with 2 Nodes on RedHat and CentOS
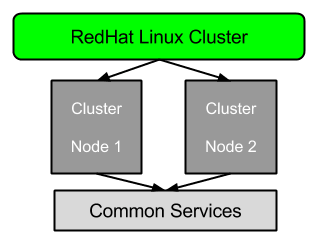
In an active-standby Linux cluster configuration, all the critical services including IP, filesystem will failover from one node to another node in the cluster.
This tutorials explains in detail on how to create and configure two node redhat cluster using command line utilities.
The following are the high-level steps involved in configuring Linux cluster on Redhat or CentOS:
- Install and start RICCI cluster service
- Create cluster on active node
- Add a node to cluster
- Add fencing to cluster
- Configure failover domain
- Add resources to cluster
- Sync cluster configuration across nodes
- Start the cluster
- Verify failover by shutting down an active node
1. Required Cluster Packages
First make sure the following cluster packages are installed. If you don’t have these packages install them using yum command.
[root@rh1 ~]# rpm -qa | egrep -i "ricci|luci|cluster|ccs|cman" modcluster-0.16.2-28.el6.x86_64 luci-0.26.0-48.el6.x86_64 ccs-0.16.2-69.el6.x86_64 ricci-0.16.2-69.el6.x86_64 cman-3.0.12.1-59.el6.x86_64 clusterlib-3.0.12.1-59.el6.x86_64
2. Start RICCI service and Assign Password
Next, start ricci service on both the nodes.
[root@rh1 ~]# service ricci start Starting oddjobd: [ OK ] generating SSL certificates... done Generating NSS database... done Starting ricci: [ OK ]
You also need to assign a password for the RICCI on both the nodes.
[root@rh1 ~]# passwd ricci Changing password for user ricci. New password: Retype new password: passwd: all authentication tokens updated successfully.
Also, If you are running iptables firewall, keep in mind that you need to have appropriate firewall rules on both the nodes to be able to talk to each other.
3. Create Cluster on Active Node
From the active node, please run the below command to create a new cluster.
The following command will create the cluster configuration file /etc/cluster/cluster.conf. If the file already exists, it will replace the existing cluster.conf with the newly created cluster.conf.
[root@rh1 ~]# ccs -h rh1.mydomain.net --createcluster mycluster rh1.mydomain.net password: [root@rh1 ~]# ls -l /etc/cluster/cluster.conf -rw-r-----. 1 root root 188 Sep 26 17:40 /etc/cluster/cluster.conf
Also keep in mind that we are running these commands only from one node on the cluster and we are not yet ready to propagate the changes to the other node on the cluster.
4. Initial Plain cluster.conf File
After creating the cluster, the cluster.conf file will look like the following:
[root@rh1 ~]# cat /etc/cluster/cluster.conf
<?xml version="1.0"?>
<cluster config_version="1" name="mycluster">
<fence_daemon/>
<clusternodes/>
<cman/>
<fencedevices/>
<rm>
<failoverdomains/>
<resources/>
</rm>
</cluster>
5. Add a Node to the Cluster
Once the cluster is created, we need to add the participating nodes to the cluster using the ccs command as shown below.
First, add the first node rh1 to the cluster as shown below.
[root@rh1 ~]# ccs -h rh1.mydomain.net --addnode rh1.mydomain.net Node rh1.mydomain.net added.
Next, add the second node rh2 to the cluster as shown below.
[root@rh1 ~]# ccs -h rh1.mydomain.net --addnode rh2.mydomain.net Node rh2.mydomain.net added.
Once the nodes are created, you can use the following command to view all the available nodes in the cluster. This will also display the node id for the corresponding node.
[root@rh1 ~]# ccs -h rh1 --lsnodes rh1.mydomain.net: nodeid=1 rh2.mydomain.net: nodeid=2
6. cluster.conf File After Adding Nodes
This above will also add the nodes to the cluster.conf file as shown below.
[root@rh1 ~]# cat /etc/cluster/cluster.conf
<?xml version="1.0"?>
<cluster config_version="3" name="mycluster">
<fence_daemon/>
<clusternodes>
<clusternode name="rh1.mydomain.net" nodeid="1"/>
<clusternode name="rh2.mydomain.net" nodeid="2"/>
</clusternodes>
<cman/>
<fencedevices/>
<rm>
<failoverdomains/>
<resources/>
</rm>
</cluster>
7. Add Fencing to Cluster
Fencing is the disconnection of a node from shared storage. Fencing cuts off I/O from shared storage, thus ensuring data integrity.
A fence device is a hardware device that can be used to cut a node off from shared storage.
This can be accomplished in a variety of ways: powering off the node via a remote power switch, disabling a Fiber Channel switch port, or revoking a host’s SCSI 3 reservations.
A fence agent is a software program that connects to a fence device in order to ask the fence device to cut off access to a node’s shared storage (via powering off the node or removing access to the shared storage by other means).
Execute the following command to enable fencing.
[root@rh1 ~]# ccs -h rh1 --setfencedaemon post_fail_delay=0 [root@rh1 ~]# ccs -h rh1 --setfencedaemon post_join_delay=25
Next, add a fence device. There are different types of fencing devices available. If you are using virtual machine to build a cluster, use fence_virt device as shown below.
[root@rh1 ~]# ccs -h rh1 --addfencedev myfence agent=fence_virt
Next, add fencing method. After creating the fencing device, you need to created the fencing method and add the hosts to the fencing method.
[root@rh1 ~]# ccs -h rh1 --addmethod mthd1 rh1.mydomain.net Method mthd1 added to rh1.mydomain.net. [root@rh1 ~]# ccs -h rh1 --addmethod mthd1 rh2.mydomain.net Method mthd1 added to rh2.mydomain.net.
Finally, associate fence device to the method created above as shown below:
[root@rh1 ~]# ccs -h rh1 --addfenceinst myfence rh1.mydomain.net mthd1 [root@rh1 ~]# ccs -h rh1 --addfenceinst myfence rh2.mydomain.net mthd1
8. cluster.conf File after Fencing
Your cluster.conf will look like below after the fencing devices, methods are added.
[root@rh1 ~]# cat /etc/cluster/cluster.conf
<?xml version="1.0"?>
<cluster config_version="10" name="mycluster">
<fence_daemon post_join_delay="25"/>
<clusternodes>
<clusternode name="rh1.mydomain.net" nodeid="1">
<fence>
<method name="mthd1">
<device name="myfence"/>
</method>
</fence>
</clusternode>
<clusternode name="rh2.mydomain.net" nodeid="2">
<fence>
<method name="mthd1">
<device name="myfence"/>
</method>
</fence>
</clusternode>
</clusternodes>
<cman/>
<fencedevices>
<fencedevice agent="fence_virt" name="myfence"/>
</fencedevices>
<rm>
<failoverdomains/>
<resources/>
</rm>
</cluster>
9. Types of Failover Domain
A failover domain is an ordered subset of cluster members to which a resource group or service may be bound.
The following are the different types of failover domains:
- Restricted failover-domain: Resource groups or service bound to the domain may only run on cluster members which are also members of the failover domain. If no members of failover domain are availables, the resource group or service is placed in stopped state.
- Unrestricted failover-domain: Resource groups bound to this domain may run on all cluster members, but will run on a member of the domain whenever one is available. This means that if a resource group is running outside of the domain and member of the domain transitions online, the resource group or
- service will migrate to that cluster member.
- Ordered domain: Nodes in the ordered domain are assigned a priority level from 1-100. Priority 1 being highest and 100 being the lowest. A node with the highest priority will run the resource group. The resource if it was running on node 2, will migrate to node 1 when it becomes online.
- Unordered domain: Members of the domain have no order of preference. Any member may run in the resource group. Resource group will always migrate to members of their failover domain whenever possible.
10. Add a Filover Domain
To add a failover domain, execute the following command. In this example, I created domain named as “webserverdomain”,
[root@rh1 ~]# ccs -h rh1 --addfailoverdomain webserverdomain ordered
Once the failover domain is created, add both the nodes to the failover domain as shown below:
[root@rh1 ~]# ccs -h rh1 --addfailoverdomainnode webserverdomain rh1.mydomain.net priority=1 [root@rh1 ~]# ccs -h rh1 --addfailoverdomainnode webserverdomain rh2.mydomain.net priority=2
You can view all the nodes in the failover domain using the following command.
[root@rh1 ~]# ccs -h rh1 --lsfailoverdomain webserverdomain: restricted=0, ordered=1, nofailback=0 rh1.mydomain.net: 1 rh2.mydomain.net: 2
11. Add Resources to Cluster
Now it is time to add a resources. This indicates the services that also should failover along with ip and filesystem when a node fails. For example, the Apache webserver can be part of the failover in the Redhat Linux Cluster.
When you are ready to add resources, there are 2 ways you can do this.
You can add as global resources or add a resource directly to resource group or service.
The advantage of adding it as global resource is that if you want to add the resource to more than one service group you can just reference the global resource on your service or resource group.
In this example, we added the filesystem on a shared storage as global resource and referenced it on the service.
[root@rh1 ~]# ccs –h rh1 --addresource fs name=web_fs device=/dev/cluster_vg/vol01 mountpoint=/var/www fstype=ext4
To add a service to the cluster, create a service and add the resource to the service.
[root@rh1 ~]# ccs -h rh1 --addservice webservice1 domain=webserverdomain recovery=relocate autostart=1
Now add the following lines in the cluster.conf for adding the resource references to the service. In this example, we also added failover IP to our service.
<fs ref="web_fs"/> <ip address="192.168.1.12" monitor_link="yes" sleeptime="10"/>
In the 2nd part of this tutorial (tomorrow), we’ll explain how to sync the configurations across multiple nodes in a cluster, and how to verify the failover scenario in a cluster setup.
Wednesday, September 2, 2015
[Mail Server]: Mail-in-a-Box: An Open Source Mail Server Solution
Mail-in-a-Box: An Open Source Mail Server Solution
About Mail-in-a-Box
Mail-in-a-Box is a free, Open Source, mail server solution developed by Joshua Tauberer.
Using Mail-in-a-Box, anyone can easily turn a fresh cloud system into a
Mail server in few hours. It can host mail for multiple users and
multiple domain names. Mail-in-a-Box is based on Ubuntu 14.04 LTS 64-bit
and includes automatic DNS configuration, spam filtering, greylisting,
backups to Amazon S3, static website hosting, and easy SSL certificate
installation.
The architecture of Mail-in-a-Box:
Install Mail-in-a-Box on Ubuntu 14.04
Requirements
To setup Mail server using Mail-in-a-Box, you must have the following requirements.
- Ubuntu 14.04 64bit VPS (Fresh installation).
- 768MB RAM or more. 1GB is recommended.
- 30GB or more Hdd free space.
- Add proper MX records in your DNS server.
- If your mail server is behind a firewall/Router, you should allow the following ports: 22 (SSH), 25 (SMTP), 53 (DNS; must be open for both tcp & udp), 80 (HTTP), 443 (HTTPS), 587 (SMTP submission), and 993 (IMAP).
Mail-in-a-Box Limitation:
Mail-in-a-Box must be installed on a fresh machine that will be dedicated to Mail-in-a-Box, and you cannot modify the box
after installation (configuration changes will get overwritten by the
box’s self-management). If you are looking for something more advanced,
try iRedMail, Sovereign, or Modoboa.
Well, now let us setup Mail-in-a-Box in Ubuntu 14.04 server.
First update your server:
sudo apt-get update
sudo apt-get upgrade
Then, run the following command to install Mail-in-a-Box
curl -s https://mailinabox.email/bootstrap.sh | sudo bash
Sample output:
Installing git . . . Selecting previously unselected package liberror-perl. (Reading database ... 55887 files and directories currently installed.) Preparing to unpack .../liberror-perl_0.17-1.1_all.deb ... Unpacking liberror-perl (0.17-1.1) ... Selecting previously unselected package git-man. Preparing to unpack .../git-man_1%3a1.9.1-1ubuntu0.1_all.deb ... Unpacking git-man (1:1.9.1-1ubuntu0.1) ... Selecting previously unselected package git. Preparing to unpack .../git_1%3a1.9.1-1ubuntu0.1_amd64.deb ... Unpacking git (1:1.9.1-1ubuntu0.1) ... Processing triggers for man-db (2.6.7.1-1ubuntu1) ... Setting up liberror-perl (0.17-1.1) ... Setting up git-man (1:1.9.1-1ubuntu0.1) ... Setting up git (1:1.9.1-1ubuntu0.1) ... Downloading Mail-in-a-Box v0.13b. . . Installing packages needed for setup... [...]
After a few minutes the following introductory message will appear. Press Enter to continue.
Enter a mail ID which will need to manage your Box later. This account will also have access to the box’s admin control panel.
Enter your FQDN name.
Select the Country where you live or where your organization is based.
Now,
sit back and relax. It will take a while to download and install all
necessary packages. During the installation, you’ll be asked to setup
Mail-in-a-Box administrative account. For example in my case, my
administrative account is sk@server.unixmen.local
Finally, you’ll see the following installation completed message:
Sample output:
Primary Hostname: server.unixmen.local Public IP Address: xxx.xxx.xx.xx Private IP Address: 192.168.1.101 Mail-in-a-Box Version: v0.13b Updating system packages... Installing system packages... Firewall is active and enabled on system startup Creating initial SSL certificate and perfect forward secrecy Diffie-Hellman parameters... Generating DH parameters, 2048 bit long safe prime, generator 2 This is going to take a long time ....................................+............+....................................................................................................................................................................................................................+.............+..........................................................................................................................+..................................................................+........+........................................................................+....................................................................................................+....+...........................................................................................................................................................+..............................................................+..................................................+.......+............................................................................................................................................................................+...................................................................................................................................................................................................+.......+............+....................................................................+...............................................++*++* Installing nsd (DNS server)... Generating DNSSEC signing keys. This may take a few minutes... Installing Postfix (SMTP server)... Installing Dovecot (IMAP server)... Creating new user database: /home/user-data/mail/users.sqlite Installing OpenDKIM/OpenDMARC... Installing SpamAssassin... Installing Nginx (web server)... Installing Roundcube (webmail)... Installing ownCloud (contacts/calendar)... creating sqlite db ownCloud is already latest version Installing Z-Push (Exchange/ActiveSync server)... Installing Mail-in-a-Box system management daemon... Installing Munin (system monitoring)... updated DNS: server.unixmen.local web updated Okay. I'm about to set up sk@server.unixmen.local for you. This account will also have access to the box's control panel. password: ## Enter the password to administrative account password (again): ## Enter the password again mail user added ----------------------------------------------- Your Mail-in-a-Box is running. Please log in to the control panel for further instructions at: https://xxx.xxx.xx.xx/admin You will be alerted that the website has an invalid certificate. Check that the certificate fingerprint matches: AC:15:B9:14:9B:BD:C6:B2:FD:98:94:75:E4:0T:14:B0:D5:F2:0G:5A Then you can confirm the security exception and continue.
Now, let us access Mail-in-a-Box admin control panel.
Access Mail-in-a-Box Control Panel
Open up your web browser and navigate to: https://domain-name/admin or https://IP-address/admin.
In
the next window, the series of system status checks will be initiated.
The System status checks will analyze all configuration including DNS
Glue records, SSH public keys, and domain name etc. If everything Ok,
all outputs will be shown in Green.
Note:
As you see in the below screenshot, There are many issues in my setup.
Because, I have setup the Mail server in my local system and haven’t add
any Glue records or any firewall rules to allow the important ports. If
you follow the same steps in your Cloud system with a public IP, you
won’t get any issues as shown below.
Creating users
To create a new user, go to Mail > Users.
The following screen should appear. Enter the username (Ex. senthil@server.unixmen.local) and it’s password.
Similarly, you can add as many users as you want.
To add an additional user to a new domain, go to Mail > Users
in the admin control panel and create mail users for your new
domain. If the email address of new user is at a new domain,
Mail-in-a-box will automatically add appropriate new settings for it.
Also, don’t forget to add proper DNS records for the New domain.
To see the current DNS settings, go to System > External DNS. To add your own entries, navigate to System > Custom DNS.
Contacts & Calendar
Mail-in-a-Box can hold your contacts and calendar, just like it holds your email.
To access Contacts, navigate to https://domain-name/cloud/contacts.
To access Calendar, navigate to https://domain-name/cloud/calendar.
Make sure you have added your Domain name in the trusted domain list.
Configure the “trusted_domain” setting in config/config.php. An example configuration is provided in config/config.sample.php.
Access Mail-in-a-Box Webmail
To access the Mail-in-a-Box web mail, navigate to: https://domain-name/mail.
The following screen should appear. Enter yhe username and it’s password which we created in the Control panel.
This is how the user’s mail box looks.
Mail-in-a-Box
uses Roundcube mail app as it’s default mail client. Now, you can
send/receive mails as the way do in the Gmail, Yahoomail accounts.
That’s for now.
For more details, refer the official Setup guide and Maintenance guide.
Also, the project founder has uploaded a video tutorial in Youtube.
Cheers!
Subscribe to:
Posts (Atom)









