IPTABLES VS FIREWALLD
What is iptables?
First, we need to know what is iptables.
Most of senior IT professionals knows about it and used to work with it
as well. Iptables is an application / program that allows a user to
configure the security or firewall security tables provided by the Linux
kernel firewall and the chains so that a user can add / remove firewall
rules to it accordingly to meet his / her security requirements.
Iptables uses different kernel modules and different protocols so that
user can take the best out of it. As for example, iptables is used for
IPv4 ( IP version 4/32 bit ) and ip6tables for IPv6 ( IP version 6/64
bit ) for both tcp and udp. Normally, iptables rules are configured by
System Administrator or System Analyst or IT Manager. You must have
root privileges to execute each iptables rules. Linux Kernel uses the
Netfilter framework so that it can provide various networking-related
operations which can be performed by using iptables. Previously,
ipchains was used in most of the Linux distributions for the same
purpose. Every iptables rules are directly handled by the Linux Kernel
itself and it is known as kernel duty. Whatever GUI tools or other
security tools you are using to configure your server’s firewall
security, at the end of the day, it is converted into iptables rules and
supplied to the kernel to perform the operation.
History of iptables
The rise of the iptables begin with
netfilter. Paul Rusty Russell was the initial author and the head think
tank behind netfilter / iptables. Later he was joined by many other tech
people then form and build the Netfilter core team and develop &
maintain the netfilter/iptables project as a joint effort like many
other open source projects. Harald Welte was the former leader until
2007 and then Patrick McHardy was the head until 2013. Currently,
netfilter core team head is Pablo Neira Ayuso.
To know more about netfilter, please visit this
link. To know more about the histrity of netfilter, please visit this
link.
To know more about iptables history, please visit this
link.
How to install iptables
Now a days, every Linux Kernel comes
with iptables and can be found pre build or pre installed on every
famous modern Linux distributions. On most Linux systems, iptables is
installed in this /usr/sbin/iptables directory. It can be also found in
/sbin/iptables, but since iptables is more like a service rather than
an “essential binary”, the preferred location remains in /usr/sbin
directory.
For Ubuntu or Debian
sudo apt-get install iptables
For CentOS
sudo yum install iptables-services
For RHEL
sudo yum install iptables
Iptables version
To know your iptables version, type the following command in your terminal.
sudo iptables --version
Start & Stopping your iptables firewall
For OpenSUSE 42.1, type the following to stop.
sudo /sbin/rcSuSEfirewall2 stop
To start it again
sudo /sbin/rcSuSEfirewall2 start
For Ubuntu, type the following to stop.
sudo service ufw stop
To start it again
sudo service ufw start
For Debian & RHEL , type the following to stop.
sudo /etc/init.d/iptables stop
To start it again
sudo /etc/init.d/iptables start
For CentOS, type the following to stop.
sudo service iptables stop
To start it again
sudo service iptables start
Getting all iptables rules lists
To know all the rules that is currently present & active in your iprables, simply open a terminal and type the following.
sudo iptables -L
If there are no rules exits on the
iptables means if there are no rules added so far in your iptables
firewall, you will see something like the below image.
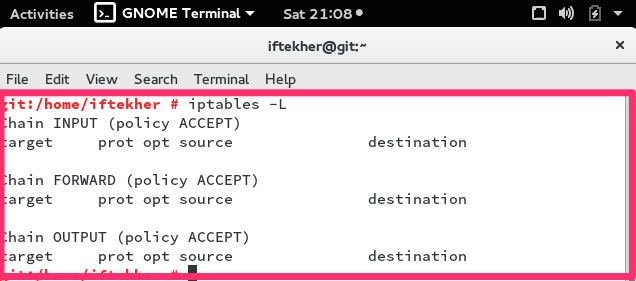
In this above picture, you can see that ,
there are three (3) chains and they are INPUT, FORWARD, OUTPUT and
there are no rules exists. Actually I haven’t add one yet.
Type the following to know the status of the chains of your iptables firewall.
sudo iptables -S
With the above command, you can learn whether your chains are accepting or not.
Clear all iptables rules
To clear all the rules from your
iptables firewall, please type the following. This is normally known as
flushing your iptables rules.
sudo iptables -F
If you want to flush the INPUT chain only, or any individual chains, issue the below commands as per your requirements.
sudo iptables -F INPUT
sudo iptables -F OUTPUT
sudo iptables -F FORWARD
ACCEPT or DROP Chains
To accept or drop a particular chain, issue any of the following command on your terminal to meet your requirements.
iptables --policy INPUT DROP
The above rule will not accept anything that is incoming to that server. To revert it again back to ACCEPT, do the following
iptables --policy INPUT ACCEPT
Same goes for other chains as well like
iptables --policy OUTPUT DROP
iptables --policy FORWARD DROP
Note: By default, all
chains of iptables ( INPUT, OUTPUT, FORWARD ) are in ACCEPT mode. This
is known as Policy Chain Default Behavior.
Allowing any port
If you are running any web server on
your host, then you must allow your iptables firewall so that your
server listen or respond to port 80. By default web server runs on port
80. Let’s do that then.
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT
On the above line, A stands for append
means we are adding a new rule to the iptables list. INPUT stands for
the INPUT chain. P stands for protocol and dport stands for destination
port. By default any web server runs on port 80. Similarly, you can
allow SSH port as well.
sudo iptables -A INPUT -p tcp --dport 22 -j ACCEPT
By default, SSH runs on port 22. But
it’s good practise not to run SSH on port 22. Always run SSH on a
different port. To run SSH on a different port, open
/etc/ssh/sshd_config file on your favorite editor and change the port 22
to a other port.
Blocking any port
Say we want to block port 135. We can do it by
sudo iptables -A INPUT -p tcp --dport 135 -j DROP
if you want to block your server to
initiate any SSH connection from the server to another host/server,
issue the following command
sudo iptables -A OUTPUT -p tcp --dport 22 -j DROP
By doing so, no one can use your sever
to initiate a SSH connection from the server. The OUPUT chain will
filter and DROP any outgoing tcp connection towards another hosts.
Allowing specific IP with Port
sudo iptables -A INPUT -p tcp -s 0/0 --dport 22 -j ACCEPT
Here -s 0/0 stand for any incoming
source with any IP addresses. So, there is no way your server is going
to respond for a tcp packet which destination port is 22. If you want to
allow only any particular IP then use the following one.
sudo iptables -A INPUT -p tcp -s 12.12.12.12/32 --dport 22 -j ACCEPT
On the above example, you are only
allowing 12.12.12.12 IP address to connect to port SSH. Rest IP
addresses will not be able to connect to port 22. Similarly you can
allow by using CIDR values. Such as
sudo iptables -A INPUT -p tcp -s 12.12.12.0/24 --dport 22 -j ACCEPT
The above example show how you can allow
a whole IP block for accepting connection on port 22. It will accept IP
starting from 12.12.12.1 to 12.12.12.255.
If you want to block such IP addresses range, do the reverse by replacing ACCEPT by DROP like the following
sudo iptables -A INPUT -p tcp -s 12.12.12.0/24 --dport 22 -j DROP
So, it will not allow to get a connection on port 22 from from 12.12.12.1 to 12.12.12.255 IP addresses.
Blocking ICMP
If you want to block ICMP (ping) request
to and from on your server, you can try the following. The first one
will block not to send ICMP ping echo request to another host.
sudo iptables -A OUTPUT -p icmp --icmp-type 8 -j DROP
Now, try to ping google.com. Your OpenSUSE server will not be able to ping google.com.
If you want block the incoming ICMP (ping) echo request for your server, just type the following on your terminal.
sudo iptables -I INPUT -p icmp --icmp-type 8 -j DROP
Now, It will not reply to any ICMP ping echo request. Say, your
server IP address is 13.13.13.13.
And if you ping ping that IP of your
server then you will see that your server is not responding for that
ping request.
Blocking MySql / MariaDB Port
As Mysql is holding your database so you must protect your database
from outside attach. Allow your trusted application server IP addresses
only to connect with your MySQL server. To block other
sudo iptables -A INPUT -p tcp -s 192.168.1.0/24 --dport 3306 -m state --state NEW,ESTABLISHED -j ACCEPT
So, it will not take any MySql connection except 192.168.1.0/24 IP block. By default MySql runs on 3306 port.
Blocking SMTP
If you not running any mail server on your host server or if your
server is not configured to act like a mail server, you must block SMTP
so that your server is not sending any spam or any mail towards any
domain. You must do this to block any outgoing mail from your server. To
do so,
sudo iptables -A OUTPUT -p tcp --dport 25 -j DROP
Block DDoS
We all are familiar with the term DDoS. To get rid of it, issue the following command in your terminal.
iptables -A INPUT -p tcp --dport 80 -m limit --limit 20/minute --limit-burst 100 -j ACCEPT
You need to configure the numerical value to meet your requirements. This is just a standard to maintain.
You can protect more by
echo 1 > /proc/sys/net/ipv4/ip_forward
echo 1 > /proc/sys/net/ipv4/tcp_syncookies
echo 0 > /proc/sys/net/ipv4/conf/all/accept_redirects
echo 0 > /proc/sys/net/ipv4/conf/all/accept_source_route
echo 1 > /proc/sys/net/ipv4/conf/all/rp_filter
echo 1 > /proc/sys/net/ipv4/conf/lo/rp_filter
echo 1 > /proc/sys/net/ipv4/conf/lo/arp_ignore
echo 2 > /proc/sys/net/ipv4/conf/lo/arp_announce
echo 1 > /proc/sys/net/ipv4/conf/all/arp_ignore
echo 2 > /proc/sys/net/ipv4/conf/all/arp_announce
echo 0 > /proc/sys/net/ipv4/icmp_echo_ignore_all
echo 1 > /proc/sys/net/ipv4/icmp_echo_ignore_broadcasts
echo 30 > /proc/sys/net/ipv4/tcp_fin_timeout
echo 1800 > /proc/sys/net/ipv4/tcp_keepalive_time
echo 1 > /proc/sys/net/ipv4/tcp_window_scaling
echo 0 > /proc/sys/net/ipv4/tcp_sack
echo 1280 > /proc/sys/net/ipv4/tcp_max_syn_backlog
Blocking Port Scanning
There are hundred of people out there to scan your open ports of your
server and try to break down your server security. To block it
sudo iptables -N block-scan
sudo iptables -A block-scan -p tcp —tcp-flags SYN,ACK,FIN,RST RST -m limit —limit 1/s -j RETURN
sudo iptables -A block-scan -j DROP
Here, block-scan is a name of a new chain.
Blocking Bad Ports
You may need to block some bad ports for your server as well. Here is how you can do this.
badport="135,136,137,138,139,445"
sudo iptables -A INPUT -p tcp -m multiport --dport $badport -j DROP
sudo iptables -A INPUT -p udp -m multiport --dport $badport -j DROP
You can add more ports according to your needs.
What is firewalld?
Firewalld provides a dynamically managed
firewall with support for network/firewall zones that defines the trust
level of network connections or interfaces. It has support for IPv4,
IPv6 firewall settings, ethernet bridges and IP sets. There is a
separation of runtime and permanent configuration options. It also
provides an interface for services or applications to add firewall rules
directly.
The former firewall model with
system-config-firewall/lokkit was static and every change required a
complete firewall restart. This included also to unload the firewall
netfilter kernel modules and to load the modules that are needed for the
new configuration. The unload of the modules was breaking stateful
firewalling and established connections. The firewall daemon on the
other hand manages the firewall dynamically and applies changes without
restarting the whole firewall. Therefore there is no need to reload all
firewall kernel modules. But using a firewall daemon requires that all
firewall modifications are done with that daemon to make sure that the
state in the daemon and the firewall in kernel are in sync. The firewall
daemon can not parse firewall rules added by the iptables and ebtables
command line tools. The daemon provides information about the current
active firewall settings via D-BUS and also accepts changes via D-BUS
using PolicyKit authentication methods.
So, firewalld uses zones and services
instead of chain and rules for performing the operations and it
can manages rule(s) dynamically allowing updates & modification
without breaking existing sessions and connections.
It has following features.
- D-Bus API.
- Timed firewall rules.
- Rich Language for specific firewall rules.
- IPv4 and IPv6 NAT support.
- Firewall zones.
- IP set support.
- Simple log of denied packets.
- Direct interface.
- Lockdown: Whitelisting of applications that may modify the firewall.
- Support for iptables, ip6tables, ebtables and ipset firewall backends.
- Automatic loading of Linux kernel modules.
- Integration with Puppet.
To know more about firewalld, please visit this
link.
How to install firewalld
Before installing firewalld, please make sure you stop iptables and
also make sure that iptables are not using or working anymore. To do so,
sudo systemctl stop iptables
This will stop iptables form your system.
And then make sure iptables are not used by your system any more by issuing the below command in the terminal.
sudo systemctl mask iptables
Now, check the status of iptables.
sudo systemctl status iptables

Now, we are ready to install firewalld on to our system.
For Ubuntu
To install it on Ubuntu, you must remove UFW first and then you can
install Firewalld. To remove UFW, issue the below command on the
terminal.
sudo apt-get remove ufw
After removing UFW, issue the below command in the terminal
sudo apt-get install firewall-applet
Or
You can open Ubuntu Software Center and look or seacrh for “firewall-applet” then install it on to your Ubuntu system.
For RHEL, CentOS & Fedora
Type the below command to install firewalld on your CentOS system.
sudo yum install firewalld firewall-config -y
How to configure firewalld
Before configuring firewalld, we must know the status of firewalld after the installation. To know that, type the following.
sudo systemctl status firewalld
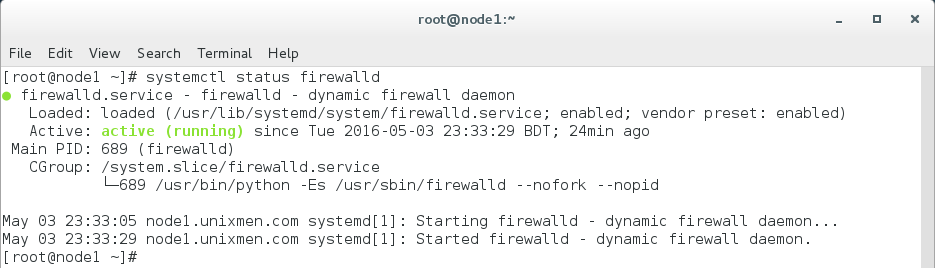
As firewalld works on zones basis, we need to check all the zones and services though we haven’t done any configuring yet.
For Zones
sudo firewall-cmd --get-active-zones
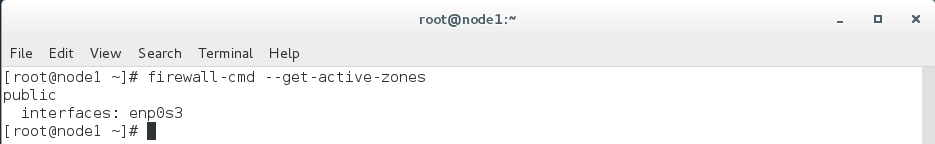
or
sudo firewall-cmd --get-zones
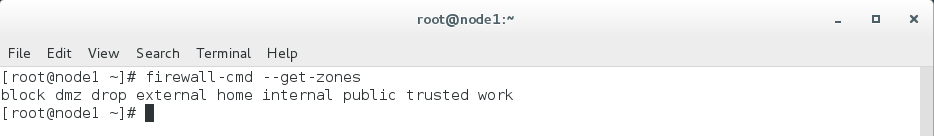
To know the default zone, issue the below command
sudo firewall-cmd --get-default-zone
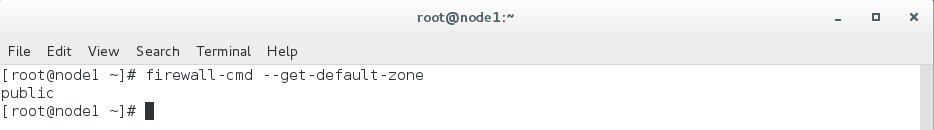
And,
For Services
sudo firewall-cmd --get-services

Here, you can see those services covered under firewalld.
Setting Default Zone
An important note is, after each modification, you need to reload firewalld so that your changes can take place.
To set the default zone
sudo firewall-cmd --set-default-zone=internal
or
sudo firewall-cmd --set-default-zone=public
After changing the zone, check whether it changes or not.
sudo firewall-cmd --get-default-zone
Adding Port in Public Zone
sudo firewall-cmd --permanent --zone=public --add-port=80/tcp
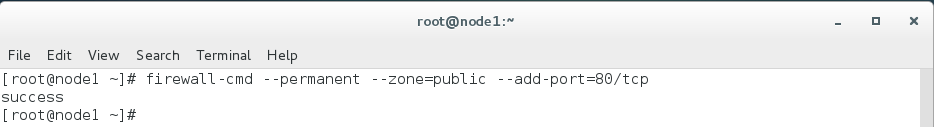
This will add tcp port 80 in the public zone of firewalld. You can add your desired port as well by replacing 80 by your’s.
Now reload the firewalld.
sudo firewall-cmd --reload
Now, check the status to see whether tcp 80 port has been added or not.
sudo firewall-cmd --zone=public --list-ports
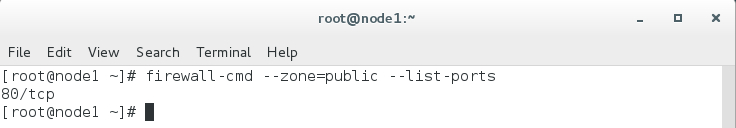
Here, you can see that tcp port 80 has been added.
Or even you can try something like this.
sudo firewall-cmd --zone=public --list-all
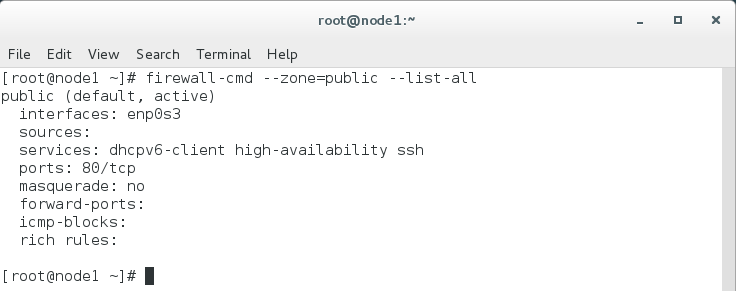
Removing Port from Public Zone
To remove Tcp 80 port from the public zone, type the following.
sudo firewall-cmd --zone=public --remove-port=80/tcp
You will see a “success” text echoing in your terminal.
You can put your desired port as well by replacing 80 by your’s own port.
Adding Services in Firewalld
To add ftp service in firewalld, issue the below command
sudo firewall-cmd --zone=public --add-service=ftp
You will see a “success” text echoing in your terminal.
Similarly for adding smtp service, issue the below command
sudo firewall-cmd --zone=public --add-service=smtp
Replace ftp and smtp by your’s own service that you want to add in the firewalld.
Removing Services from Firewalld
For removing ftp & smtp services from firewalld, issue the below command in the terminal.
sudo firewall-cmd --zone=public --remove-service=ftp
sudo firewall-cmd --zone=public --remove-service=smtp
Block Any Incoming and Any Outgoing Packet(s)
If you wish, you can block any incoming or outgoing packets /
connections by using firewalld. This is known as “panic-on” of
firewalld. To do so, issue the below command.
sudo firewall-cmd --panic-on
You will see a “success” text echoing in your terminal.
After doing this, you will not be able to ping a host or even browse any websites.
To turn this off, issue the below command in your terminal.
sudo firewall-cmd --panic-off
Adding IP Address in Firewalld
sudo firewall-cmd --zone=public --add-rich-rule='rule family="ipv4" source address="192.168.1.4" accept'
By doing so, firewalld will accept IP v4 packets from the source IP 192.168.1.4.
Blocking IP Address From Firewalld
Similarly, to block any IP address
sudo firewall-cmd --zone=public --add-rich-rule='rule family="ipv4" source address="192.168.1.4" reject'
By doing so, firewalld will drop / discards every IP v4 packets from the source IP 192.168.1.4.













