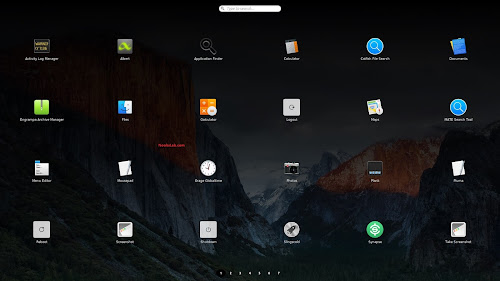
MacBuntu 16.10 Transformation Pack for Ubuntu 16.10 Yakkety
MacBuntu
(Macbuntu Yosemite/El Capitan) transformation pack is ready to take off
and land on your Ubuntu 16.10 Yakkety Yak. It offers two themes for GTK
(which supports: Unity, Gnome, Cinnamon, Mate and Xfce), one theme for
Gnome Shell, one for Cinnamon, two icon packs, and cursors. Unlike last
time we are not sharing boot/splash for macbuntu and theme for
lightdm-webkit because there are some issues within the Ubuntu 16.10.
Slingscold which is known as launchpad, it does work on some desktops
but it may don't work for some users and you may see blank launcher. We
are using and recommending Plank dock with this pack because it is
lightweight and works with all desktops without any issues. Also credit
goes to Jared
for helping us with this transformation pack. By following these
instructions you can change look of your Ubuntu 16.10 Yakkety to look
like Mac. In previous packs we used LightDM webkit theme which looks
quite similar to Mac OS X login screen, this time we aren't offering,
because we experienced a lot of issues after installing it (like: not
able to login/blank screen). Also Bootscreen has some issues.
As
we always recommend to transform your desktop by yourself, so you know
what you are doing and can reverse it easily, we can make automatic or
semi-automatic scripts but it will be only for one desktop and it won't
be good idea that's why are not automating it. By offering this pack no
hate or infringing behavior is intended, simply designed for those who
don't want to use Mac or can't use Mac for any reason.
Note: If you encounter any bug in theme/icons/any stuff, report to us with screenshot or problem with details.
>> MacBuntu Pack For Ubuntu 16.04 Xenial Xerus/Linux Mint 18
>> MBuntu Pack For Ubuntu 14.04 Trusty Tahr/Linux Mint 17
>> MacBuntu Pack For Ubuntu 14.04 Trusty Tahr/Linux Mint 17
>> MacBuntu Pack For Ubuntu 12.04 Precise Pangolin/Linux Mint 13
What's in this Version?
- A PPA dedicated to Macbuntu packs.
- Themes are better coded from scratch, looks shiny, smooth, fast
- GTK themes supports Unity, Mate, Gnome, Xfce, Cinnamon
- Theme for Gnome Shell, and one for Cinnamon
- Icon huge update for 16.10
- Four Plank dock themes
- Latest Cursor theme
1: MacBuntu wallpapers
Download MacBuntu OS Wallpapers and extract to pictures directory.2: MacBuntu OS Y Theme, Icons and cursors:
Enter these commands in terminal to get themes, icons and cursors.
To Uninstall themes, icons and cursors
3: Slingscold (Alternative to Launchpad)
To install Slingscold Launcher (Launchpad) in Ubuntu/Linux Mint open Terminal (Press Ctrl+Alt+T) and copy the following commands in the Terminal:
4: Albert Spotlight (Alternative to Mac Spotlight)
Albert
alternative to OS-X spotlight created by Manuel, it offers pretty much
same features like Spotlight or maybe better than Spotlight. It is a
selection-based search system, which creates an index of all items and
files on the system. It is designed to allow the user to quickly locate a
wide variety of items on the computer, including documents, pictures,
music, applications, and System Preferences. You can set custom hotkey
and modify search criteria for albert.
5: Plank Dock
This time we chose Plank it seems a best choice for this pack because it doesn't have any kind of issues, it is lightweight and we are providing themes with this pack for Plank dock.First of all install Plank dock with following command then install Mac themes for Plank:
Install themes for Plank dock, enter following commands in terminal:
Use these commands to remove Plank dock themes from your system:
Enter following command to remove Plank dock and themes:
Tip: To pin application to dock just open Application and right click on app icon then select 'Keep in dock'.
6: Replace 'Ubuntu Desktop' text with 'Mac' on the Panel
Enter following commands to change 'Ubuntu Desktop' text on the panel:
Revert back to 'Ubuntu Desktop' text, enter following commands in the Terminal:
7: Apple Logo in Launcher
Enter following commands to install Apple Logo:
If you want back Ubuntu logo enter following commands in terminal:
8: Tweak Tools to change Themes & Icons:
You can use these popular tools to change themes and icons in Ubuntu, Also you can change other settings from these tweak tools.Enter following command to install tweak tools.
9: Install Monochrome icons for Libreoffice:
Human icons are default in LibreOffice which kind of look weird with this transformation pack, to make LibreOffice more elegant with monochrome icons follow these instructions.Enter following commands to install monochrome icons for libreoffice.
10: (Optional) Mac fonts:
Last time I received request about Mac fonts, so this time I am including them with this pack. So here are fonts for you.You can change fonts from Unity-Tweak-Tool, Gnome-Tweak-Tool.