Access Control ListsThe importance of access controls cannot be overstated. It is important to have a good understanding of how to control who uses squid. When access controls are created you will use two components. The first is the acl which defines, clients, IP Addresses, hostnames, origin port numbers and request methods. Once these are created they are combined with rules for the acls.
The acls are created using a basic structure.
acl name type value
Here is an example which shows the name as “net”, the type is “src” which is the source and the vlaue is the network address.
acl net src 192.168.7.0/24
ACL Types
There are about 25 acl types which can be used.
There are about 25 acl types which can be used.
src, dst, myip
Several types use ip addresses as a value. The following three examples are all acceptable to squid. Squid will try to calculate the subnet if it is not included, however, it is a good practice to add the correct subnet when the acl is written.
Several types use ip addresses as a value. The following three examples are all acceptable to squid. Squid will try to calculate the subnet if it is not included, however, it is a good practice to add the correct subnet when the acl is written.
acl net src 192.168.7.0/24
acl net src 192.168.7.0/255.255.255.0
acl net src 192.168.7.0
acl net src 192.168.7.0/255.255.255.0
acl net src 192.168.7.0
Hostnames may be used in the acls but this is not a god idea and squid will convert hostnames on startup but will not make DNS lookups after that so if the address of the host changes it will be incorrect.
src
The src is the source or where the request is coming from.
The src is the source or where the request is coming from.
acl myworkstation src 192.168.7.56
Here the source is the specific ip address of 192.168.7.56.
dst
dst is where the request is directed at. One of the problems of using dst is that it must make a host lookup before it can process the request and this may take too long. Better to use dstdomain.
dst is where the request is directed at. One of the problems of using dst is that it must make a host lookup before it can process the request and this may take too long. Better to use dstdomain.
myip
This type is useful only when squid will use several ip addresses. It is used to indicate which ip address for squid to use. This may be very useful for setting up squid so that it will listen on two separate networks with different ip addresses.
This type is useful only when squid will use several ip addresses. It is used to indicate which ip address for squid to use. This may be very useful for setting up squid so that it will listen on two separate networks with different ip addresses.
srcdomian, dstdomain, cache_host_domain
These types use domain names. Be careful with domain names because of the difference between domain names and subdomains. If the acl begins with a “.” then it is used as a wildcard and it will
match all domains and subdomians. If it is without the “.”, then it will be considered an exact match.
These types use domain names. Be careful with domain names because of the difference between domain names and subdomains. If the acl begins with a “.” then it is used as a wildcard and it will
match all domains and subdomians. If it is without the “.”, then it will be considered an exact match.
acl example1 srcdomain example.com
acl example2 srcdomain .example.com
acl example2 srcdomain .example.com
In the examples above the acl example1 will not match mail.example.com nor www.example.com because it must be an exact match. However,
mail.example.com, www.example.com and example.com all will match the second acl.
mail.example.com, www.example.com and example.com all will match the second acl.
The differences between dst and dstdomain.
The dst type only checks the domain one time, so that if it changes you will not have the correct information. However, when using dstdomain, squid will check it every time it is accessed, which is a
safer situation.
The dst type only checks the domain one time, so that if it changes you will not have the correct information. However, when using dstdomain, squid will check it every time it is accessed, which is a
safer situation.
srcdomain
The srcdomain will force squid to do a reverse DNS lookup to verify the IP Address. If a domain is not configured correctly, then it will not be able to complete the reverse lookup and fail. This is the biggest
drawback to using srcdomain.
ident, proxy_auth
These two types use usernames.
srcdom_regex, dstdom_regex, url_regex, urlpath_regex,
browser, referer_regex, ident_regex, proxy_auth_regex,
req_mime_type, rep_mime_type
The srcdomain will force squid to do a reverse DNS lookup to verify the IP Address. If a domain is not configured correctly, then it will not be able to complete the reverse lookup and fail. This is the biggest
drawback to using srcdomain.
ident, proxy_auth
These two types use usernames.
srcdom_regex, dstdom_regex, url_regex, urlpath_regex,
browser, referer_regex, ident_regex, proxy_auth_regex,
req_mime_type, rep_mime_type
^http://
The regular expression matches any URL that begins with http://.
The regular expression matches any URL that begins with http://.
\.jpg$
The regular expression matches any file extension that ends in .jpg.
the \ is added because “.” is also a wildcard.
The regular expression matches any file extension that ends in .jpg.
the \ is added because “.” is also a wildcard.
acl net url_regex ^http://www
Squid is case sensitive by default. In order to make it
case insensitive use the -i option.
case insensitive use the -i option.
acl net url_regex -i ^http://www
port, myport
The port number is a number that is used by a service on a server or workstation to communicate with another service.
The port number is a number that is used by a service on a server or workstation to communicate with another service.
acl net port 22
acl net port 20-21
acl net port 20-21
port
Ports are an area to be careful with. The best configuration will deny all ports and only allow those determined to be safe. The configuration below allows only ports 21,80.443,1209 and unregistered ports. Port 21 is used
for ftp, port 80 for web services, port 443 for encrypted sites and port 1209 is a special port used for a web
based learning site. Unregistered ports are ports that are used to connect to services on the Internet and are generally accepted as safe when they are outgoing ports.
Ports are an area to be careful with. The best configuration will deny all ports and only allow those determined to be safe. The configuration below allows only ports 21,80.443,1209 and unregistered ports. Port 21 is used
for ftp, port 80 for web services, port 443 for encrypted sites and port 1209 is a special port used for a web
based learning site. Unregistered ports are ports that are used to connect to services on the Internet and are generally accepted as safe when they are outgoing ports.
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 1209 # plato
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 1209 # plato
acl Safe_ports port 1025-65535 # unregistered ports
http_access deny !Safe_ports
myport
Myport is used when a squid server may receive different types of requests for specific services. For example if the squid server was accepting connections as a proxy for users and also accepting connections as a HTTP accelerator.
Myport is used when a squid server may receive different types of requests for specific services. For example if the squid server was accepting connections as a proxy for users and also accepting connections as a HTTP accelerator.
acl accelerator myport 80
acl proxy myport 3128
acl net src 192.168.7.0/24
acl proxy myport 3128
acl net src 192.168.7.0/24
=======================================================================
Dansguardian Content Filter
Dansguardian is a content filter that is easy to set up and configure with your preferences including the ability to scan http access with clamav. The main concept behind content filtering is that the application will read the text, evaluate images and types of file extensions before the client has access. This has the advantage of stopping unacceptable content before the user has access and preventing harmful file access.
sudo apt-get install dansguardian clamav-daemon
Once Dansguardian is installed you will have a directory /etc/dansguardian that shows this content.
authplugins dansguardian.conf downloadmanagers lists
contentscanners dansguardianf1.conf languages
authplugins dansguardian.conf downloadmanagers lists
contentscanners dansguardianf1.conf languages
The ,main configuration file is dansguardain.conf. This file needs to be modified so that this line is either commented out or removed.
#UNCONFIGURED – Please remove this line after configuration
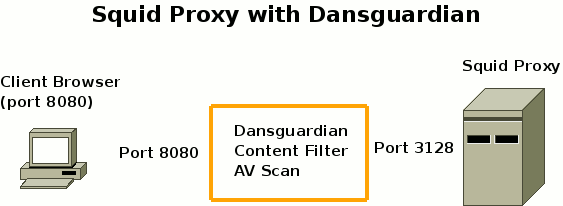
You do not need to make any other adjustments to this configuration file to get it to work. As you can see below, once you implement Dansguardian you will be using two ports, 3128 so that Dansguardian can talk to Squid and port 8080 so the client can talk to Dansguardian. The illustration shows how this works. The important implication is that you now need to alter the client so it listens on port 8080 not 3128.
filterip =
# the port that DansGuardian listens to.
filterport = 8080
# the ip of the proxy (default is the loopback – i.e. this server)
proxyip = 127.0.0.1
# the port DansGuardian connects to proxy on
proxyport = 3128
# the port that DansGuardian listens to.
filterport = 8080
# the ip of the proxy (default is the loopback – i.e. this server)
proxyip = 127.0.0.1
# the port DansGuardian connects to proxy on
proxyport = 3128
You should see that the server is listening on two ports with netstat.
netstat -aunt
tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN
tcp 0 0 0.0.0.0:8080 0.0.0.0:* LISTEN
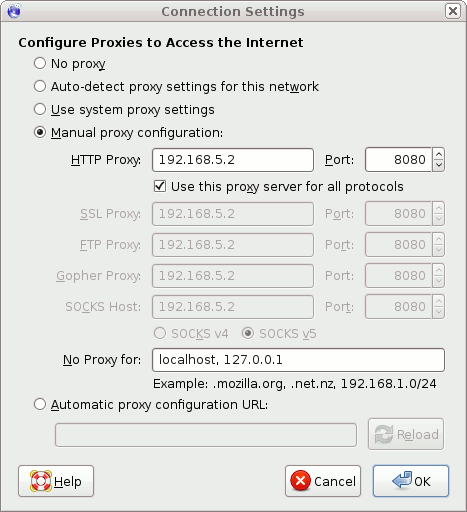
Once you have commented out the necessary line in the dansguardian.conf you must restart squid and Dansguardian. Next, adjust your client to listen on the correct port.
Here is the client adjusted to listen on port 8080.
You also have the ability to scan files for virus activity with clamav. Check to see if clamav is available with this command.
ps -ef | grep clamav
clamav 14054 1 0 07:00 ? 00:00:00 /usr/bin/freshclam -d –quiet
clamav 14978 1 0 14:27 ? 00:00:00 /usr/sbin/clamd
clamav 14054 1 0 07:00 ? 00:00:00 /usr/bin/freshclam -d –quiet
clamav 14978 1 0 14:27 ? 00:00:00 /usr/sbin/clamd
Content Management
The configuration files in /etc/dansguardian, dansguardain.conf and dansguardianf1.conf are both well commented and provide a lot of options. In the dansguardian.conf you will find these options that are commonly adjusted.
The configuration files in /etc/dansguardian, dansguardain.conf and dansguardianf1.conf are both well commented and provide a lot of options. In the dansguardian.conf you will find these options that are commonly adjusted.
You can either block all downloads or follow the lists and select specific file types you will not all ow to be downloaded.
blockdownloads = off
exceptionextensionlist = ‘/etc/dansguardian/lists/exceptionextensionlist’
exceptionmimetypelist = ‘/etc/dansguardian/lists/exceptionmimetypelist’
bannedextensionlist = ‘/etc/dansguardian/lists/bannedextensionlist’
bannedmimetypelist = ‘/etc/dansguardian/lists/bannedmimetypelist’
blockdownloads = off
exceptionextensionlist = ‘/etc/dansguardian/lists/exceptionextensionlist’
exceptionmimetypelist = ‘/etc/dansguardian/lists/exceptionmimetypelist’
bannedextensionlist = ‘/etc/dansguardian/lists/bannedextensionlist’
bannedmimetypelist = ‘/etc/dansguardian/lists/bannedmimetypelist’
The content is rated using a numbering system, which you can adjust, and once content is evaluated and goes over the “naughtynesslimit” the content is denied. So you can adjust the number which is that top limit with this setting, increase the number for greater access.
naughtynesslimit = 50
The lists directory contains a list of files that can be adjusted to your requirements. These files include text files that are easy to adjust in terms of ratings for terms, file types, etc. The files are one of three types; banned, exceptions or lists of terms and weights for those terms. These should be easy enough to modify as they are heavily comments.
No comments:
Post a Comment